Self Securing Storage
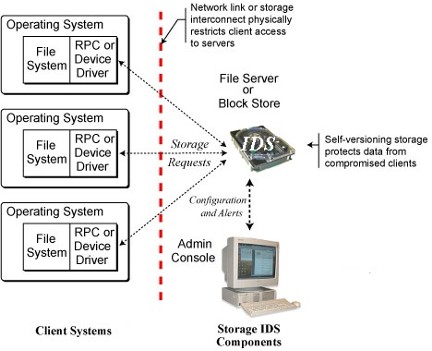
The
compromise independence of self-securing storage. The storage
interface provides
a physical boundary between a storage server
and client OSes. Note that this same
picture works for block
protocols, such as SCSI or IDE/ATA, and distributed file system
protocols such as NFS or CIFS.
Self-securing storage is an exciting new technology
for enhancing intrusion survival by enabling the storage device to
safeguard data even when the client OS is compromised. It capitalizes
on the fact that storage servers (whether file servers, disk array
controllers, or even IDE disks) run separate software on separate
hardware. This opens the door to server-embedded security that cannot
be disabled by any software (even the OS) running on client systems
as shown in the figure above. Of course, such servers have a narrow
view of system activity, so they cannot distinguish legitimate users
from clever impostors. But, from behind the thin storage interface,
a self-securing storage server can actively look for suspicious behavior,
retain an audit log of all storage requests, and prevent both destruction
and undetectable tampering of stored data. The latter goals are achieved
by retaining all versions of all data; instead of over-writing old
data when a write command is issued, the storage server simply creates
a new version and keeps both. Together with the audit log, the server-retained
versions represent a complete history of system activity from the
storage system’s point of view.
People
FACULTY
STAFF
Greg Economou
STUDENTS
Garth Goodson
Adam Pennington
Craig Soules
John Strunk
Publications
SELF SECURING STORAGE
- The Safety and Liveness Properties of a Protocol Family for Versatile Survivable Storage Infrastructures. Garth R. Goodson, Jay J. Wylie, Gregory R. Ganger, Michael K. Reiter. Carnegie Mellon University Parallel Data Laboratory Technical Report CMU-PDL-03-105. March 2004.
Abstract / Postscript [922K] / PDF [227K]
- Efficient Consistency for Erasure-coded Data via Versioning Servers.
Garth R. Goodson, Jay J. Wylie, Gregory R. Ganger, Michael K. Reiter.
Carnegie Mellon University Technical Report CMU-CS-03-127, April 2003.
Abstract / Postscript [290K] / PDF [160K]
- Storage-based
Intrusion Detection: Watching Storage Activity For Suspicious Behavior
Adam Pennington, John Strunk, John Griffin, Craig Soules, Garth Goodson & Greg Ganger. 12th USENIX Security Symposium, Washington, D.C., Aug 4-8, 2003. Also available as Carnegie Mellon University Technical Report CMU-CS-02-179, September 2002.
Abstract / Postscript [727K] / PDF [138K]
- Metadata Efficiency in a Comprehensive Versioning File System. Craig A. N. Soules, Garth R. Goodson, John D. Strunk, Gregory R. Ganger.
2nd USENIX Conference on File and Storage Technologies, San Francisco,
CA, Mar 31 - Apr 2, 2003. Also available as CMU SCS Technical Report
CMU-CS-02-145, May 2002.
Abstract / Postscript [817K] / PDF [178K]
- Intrusion Detection, Diagnosis, and Recovery with Self-Securing
Storage. John D. Strunk, Garth R. Goodson, Adam G. Pennington,
Craig A.N. Soules, Gregory R. Ganger. CMU SCS Technical Report CMU-CS-02-140,
May 2002.
Abstract / Postscript [1.1M] / PDF [119K]
- Self-Securing Storage: Protecting Data in Compromised Systems. Strunk, J.D., Goodson, G.R., Scheinholtz, M.L., Soules, C.A.N. and
Ganger, G.R. Appears in Proc. of the 4th Symposium on Operating Systems
Design and Implementation (San Diego, CA, 23-25 October 2000), pages
165-180. USENIX Association, 2000.
Abstract / Postscript [345K] / PDF [294K]