Self Securing Devices: Extended Overview
Better Security via Smarter Devices:
Seige
Warfare in the Internet Age

Despite enormous effort and investment, it has proven nearly impossible
to prevent computer security breaches. Between growing dependence upon
on-line information and wide-area networking, an enormous security risk
to our national economic and defense infrastructures exists. To protect
critical information infrastructures, we need defenses that can survive
determined and successful attacks, allowing security managers to dynamically
detect, diagnose, and recover from breaches in security perimeters.
To attack the security dilemma, the PDL has embarked on a long-term research effort to re-architect computer systems into “Self-Securing Devices.” Funded by the Department of Defense’s Critical Infrastructure Protection program, we draw on our experience with Network-Attached Storage, Self-Securing Storage, PASIS, and Scalable Firewalls, to promote a security architecture where individual system components erect their own security perimeters and protect their resources (e.g., network, storage, or video feed) from intruder tampering. The “self-securing devices” architecture distributes security functionality amongst physically distinct components, avoiding much of the fragility and manageability inherent in today’s border-based security.
Specifically, this new architecture addresses three fundamental difficulties: it simplifies each security perimeter (e.g., NIC or disk interfaces), it reduces the power that an intruder gains from compromising just one of the perimeters, and (3) it distributes security enforcement checks among the many components of the system.
Current security mechanisms (figure 1) are based largely on singular border protections. This roughly corresponds to defense practices during Roman times, when defenders erected walls around their camps and homes to provide protective cover during attacks. Once inside the walls, however, attackers faced few obstacles to gaining access to all parts of the enclosed area. Likewise, a cracker who successfully compromises a firewall or OS has complete access to the resources protected by these border defenses. Of course, border defenses were a large improvement over open camps, but they proved difficult to maintain against determined attackers – border protections can be worn down over time and defenders are often spread thin at the outer wall.
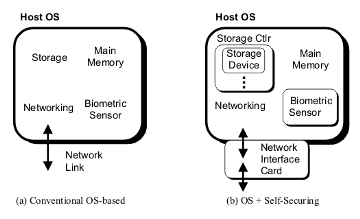
Figure 1: Two security approaches for a computer
system. On the left, (a) shows the conventional approach, which is
based on a single perimeter around the set of system resources. On
the right, (b) shows our new approach, which augments the conventional
security perimeter with perimeters around each self-securing device.
These additional perimeters offer additional protection and flexibility
for defense against attackers. Firewall-enforced network security
fits a similar picture, with the new paradigm providing numerous new
security perimeters within each system on the internal network.
As the size and sophistication of attacking forces grew, so did the sophistication of defensive structures. The most impressive such structures, constructed to withstand determined sieges in medieval times, used multiple tiers of defenses. Further, tiers were not strictly hierarchical in nature – rather, some structures could be defended independently of others. This major advancement in defense capabilities provided defenders with significant flexibility in defense strategy, the ability to observe attacker activities, and the ability to force attackers to deal with multiple independent defensive forces.
Applying the same ideas to computer and network security, border protections (i.e., firewalls and host OSes) can be augmented with security perimeters erected at many points within the borders. Enabled by low-cost computation (e.g., embedded processors, ASICs), security functionality can be embedded in most device microcontrollers, yielding “better security via smarter devices.” We refer to devices with embedded security functionality as self-securing devices (figure 2).
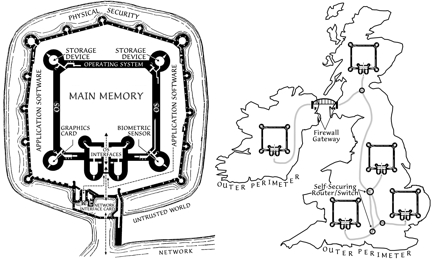
Figure 2: The self-securing device paradigm
illustrated via the siege warfare constructs that inspired it. On
the left, (a) shows a siege-ready system with layered and independent
tiers of defense enabled by device-embedded security perimeters. On
the right, (b) shows two small intranets of such systems, separated
by firewall-guarded entry points. Also note the self-securing routers/switches
connecting the machines within each intranet.
Self-securing devices can significantly increase network security and manageability, enabling capabilities that are difficult or impossible to implement in current systems. For example, independent device-embedded security perimeters guarantee that a penetrated boundary does not compromise the entire system. Uncompromised components continue their security functions even when other system components are compromised. Further, when attackers penetrate one boundary and then attempt to penetrate another, uncompromised components can observe and react to the intruder’s attack; from behind their intact security perimeters, they can send alerts to the security administrator, actively quarantine or immobilize the attacker, and wall-off or migrate critical data and resources. Pragmatically, each self-securing device’s security perimeter is simpler because of specialization, which should make correct implementations more likely. Further, distributing security checks among many devices reduces their performance impact and allows more checks to be made.
By augmenting conventional border protections with self-securing devices,
substantial increases in both network security and security manageability
can result. As with medieval fortresses, well-defended systems conforming
to this architecture could survive protracted sieges by organized attackers
.
Device-Embedded Security Examples
Network Interface Cards: NICs in computer systems move packets between the system's components and the network. Thus, the natural security extension is to enforce security policies on packets forwarded in each direction. Like a firewall, a self-securing NIC does this by examining packet headers and simply not forwarding unacceptable packets into or out of the computer system. A self-securing NIC can also act as a machine-specific gateway proxy, achieving the corresponding protections without scalability or identification problems; by performing such functions at each system’s NIC, one avoids the bottleneck imposed by current centralized approaches.
Storage Devices: The role of storage devices in computer systems is to persistently store data. Thus, the natural security extension is to protect stored data from attackers, preventing undetectable tampering and permanent deletion. Self-securing storage devices do this by managing storage space from behind its security perimeter, keeping an audit log of all requests, and keeping clean versions of data modified by attackers. Since a storage device cannot distinguish compromised user accounts from legitimate users, the latter requires keeping all versions of all data. Finite capacities limit how long such comprehensive versioning can be maintained, but 100% per year storage capacity growth will allow modern disks to keep several weeks of all versions. If intrusion detection mechanisms reveal an intrusion within this detection window, security administrators will have this valuable audit and version information for diagnosis and recovery.
Biometric Sensors: Biometric sensors provide input to biometric-enhanced authentication processes, which promise to distinguish between users based on measurements of their physical features. The natural security extension is to ensure the authenticity of the information provided to these processes. A self-securing sensor can do this by timestamping and digitally signing its sensor information. Such evidence of when and where readings were taken is critical to secure use of biometric information because, unlike passwords, biometrics are not secrets. For example, anyone can lift fingerprints from a laptop with the right tools or download facial images from a web page. Thus, evidence is needed to prevent straightforward forgery and replay attacks. Powerful self-securing sensors may also be able to increase security and privacy by performing the identity verification step from within their security perimeter and only exposing the results (with the evidence). By embedding mechanisms for demonstrating authenticity and timeliness inside sensor devices, one can verify sensor information (even over a network) even when intruders gain the ability to offer their own “sensor” data.
Graphical Displays: The role of graphical displays to visually present information to users. Thus, a natural security extension would be to ensure that critical information is displayed. A self-securing display could do this by allowing high-privilege entities to display data that cannot be overwritten or blocked by less-privileged entities. Thus, a security administrator could display a warning message when there is a problem in the system (e.g., a suspected trojan horse or a new e-mail virus that must not be opened). By embedding this screen control inside the display device, one gains the ability to ensure information visibility even when an intruder gains control over the window manager.
Routers and Switches: The role of routers and switches in a network environment is to forward packets from one link to an appropriate next link. Thus, a natural security extension for such devices is to provide firewall and proxy functionality. Many current routers already provide this. Some routers/switches also enhance security by isolating separate virtual LANs (VLANs). More dynamic defensive actions could provide even more defensive flexibility and strength. For example, the ability to dynamically change VLAN configurations would give security administrators the ability to create protected command and control channels in times of crisis or to quarantine areas suspected of compromise. When under attack, self-securing routers/switches could also initiate transparent replication of data services, greatly reducing the impact of denial-of-service attacks. Further, essential data sites could be replicated on-the-fly to “safe locations” or immediately isolated via VLANs to ensure security.